The .htaccess file is a powerful yet often underutilized tool for enhancing your WordPress website’s security, performance, and functionality. By adding or modifying directives in this file, you can protect your website from attacks, optimize performance, and enforce best practices.
This cheat sheet is designed to help you create the ultimate .htaccess configuration for your WordPress site. Let’s dive in!
1. Core WordPress Configuration
Every WordPress site needs a set of rewrite rules for permalinks to work properly. These rules are often generated automatically.
WordPress Rewrite Rules
# BEGIN WordPress Core Rules
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization}]
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPress Core Rules2. Enforce HTTPS
Ensure all traffic is redirected to HTTPS to secure communication between your server and visitors.
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{HTTPS} !=on
RewriteRule ^ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
</IfModule>3. Block Access to Sensitive Files
Prevent access to critical WordPress files like wp-config.php, .htaccess, and readme.html that might expose sensitive information.
<FilesMatch "^(wp-config\.php|install\.php|readme\.html|error_log|\.htaccess|\.htpasswd)$">
Order Allow,Deny
Deny from all
</FilesMatch>4. Disable XML-RPC
If you’re not using XML-RPC, disable it to protect your website from brute-force and DDoS attacks.
<IfModule mod_rewrite.c>
RewriteCond %{REQUEST_URI} ^/xmlrpc.php [NC]
RewriteRule .* - [F,L]
</IfModule>5. Block Access to the Includes Folder
WordPress includes files are not meant to be accessed directly. Block access to the wp-admin/includes folder and other critical directories.
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ - [F,L]
RewriteRule !^wp-includes/ - [S=3]
RewriteRule ^wp-includes/[^/]+\.php$ - [F,L]
RewriteRule ^wp-includes/js/tinymce/langs/.+\.php - [F,L]
RewriteRule ^wp-includes/theme-compat/ - [F,L]
</IfModule>6. Protect Against Malicious Requests
Block malicious query strings and HTTP methods to prevent common web attacks.
Block Malicious Query Strings
<IfModule mod_rewrite.c>
RewriteCond %{QUERY_STRING} (eval\() [NC,OR]
RewriteCond %{QUERY_STRING} (base64_encode) [NC,OR]
RewriteCond %{QUERY_STRING} (GLOBALS|REQUEST)(=|\[|%) [NC,OR]
RewriteCond %{QUERY_STRING} (<|%3C)(.*)script(.*)(>|%3) [NC,OR]
RewriteCond %{QUERY_STRING} (\.\./|\.\.\\) [NC,OR]
RewriteCond %{QUERY_STRING} (boot\.ini|etc/passwd|self/environ) [NC]
RewriteRule .* - [F]
</IfModule>Block Bad HTTP Methods
<IfModule mod_rewrite.c>
RewriteCond %{REQUEST_METHOD} ^(connect|debug|move|put|trace|track) [NC]
RewriteRule .* - [F]
</IfModule>7. Prevent Hotlinking
Stop other websites from embedding your images directly, which saves bandwidth and protects your assets.
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^https?://%{HTTP_HOST} [NC]
RewriteCond %{REQUEST_FILENAME} -f
RewriteRule \.(jpg|jpeg|png|gif|bmp|webp)$ - [F,L]
</IfModule>and if you want to Serve a Custom “No Hotlinking” Image
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^https?://%{HTTP_HOST} [NC]
RewriteCond %{REQUEST_FILENAME} -f
RewriteRule \.(jpg|jpeg|png|gif|bmp|webp)$ /path/to/anti-hotlink-image.png [R=302,L]
</IfModule>Replace /path/to/anti-hotlink-image.png with the actual path to your custom image.
8. Security Headers
Content Security Policy (CSP)
<IfModule mod_headers.c>
Header set Content-Security-Policy "upgrade-insecure-requests;"
</IfModule>Ensures all resources are loaded securely, mitigating XSS attacks.
Referrer Policy
<IfModule mod_headers.c>
Header set Referrer-Policy "no-referrer"
</IfModule>Limits how much referrer data is shared.
X-Frame-Options
<IfModule mod_headers.c>
Header set X-Frame-Options "sameorigin"
</IfModule>Prevents clickjacking attacks.
X-XSS-Protection
<IfModule mod_headers.c>
Header set X-XSS-Protection "1; mode=block"
</IfModule>Provides basic XSS protection.
Permissions Policy
<IfModule mod_headers.c>
Header set Permissions-Policy "geolocation=(), midi=(), accelerometer=(), gyroscope=(), magnetometer=(), payment=(), camera=(), microphone=(), usb=(), fullscreen=(self)"
</IfModule>Restricts browser features for better privacy.
Strict Transport Security (HSTS)
<IfModule mod_headers.c>
Header always set Strict-Transport-Security "max-age=31536000; includeSubDomains; preload"
</IfModule>Enforces HTTPS and improves performance.
9. Performance Optimization
Enable Gzip Compression
<IfModule mod_deflate.c>
AddOutputFilterByType DEFLATE text/html text/plain text/xml text/css application/javascript application/json
</IfModule>Compresses resources to improve load times.
Disable Directory Listing
Options All -IndexesHides directory structures from public view.
Remove PHP Version Exposure
Header always unset X-Powered-ByHides your server’s PHP version for security.
10. Bonus: LiteSpeed Cache Rules
If you’re using LiteSpeed Cache, include these rules:
<IfModule LiteSpeed>
RewriteEngine on
CacheLookup on
RewriteRule .* - [E=Cache-Control:no-autoflush]
RewriteRule litespeed/debug/.*\.log$ - [F,L]
</IfModule>Test Your Configuration
After implementing the .htaccess rules:
- Test your website: Ensure it loads correctly.
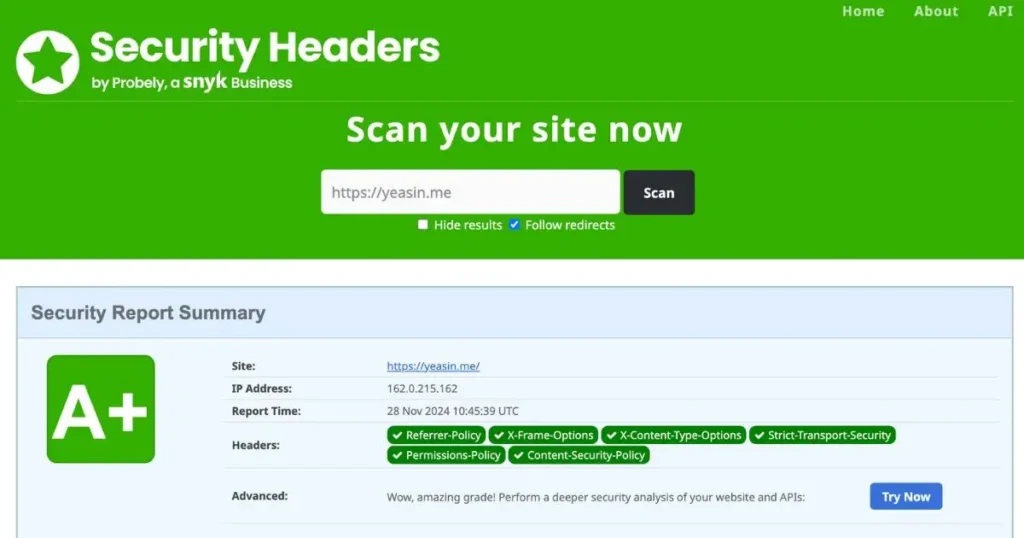
- Use Tools: Check your headers using securityheaders.com.
- Monitor Console Logs: Look for CSP or header-related errors in browser dev tools.
The .htaccess file is a powerful tool that can transform the way your WordPress website operates, making it faster, more secure, and better optimized. From preventing unauthorized access to blocking malicious bots and enforcing HTTPS, this cheat sheet equips you with essential rules to take full control of your site. Whether you’re a WordPress beginner or a seasoned developer, implementing these .htaccess configurations can help you stay ahead in website security and performance. Remember, always back up your site and test changes thoroughly before applying them to ensure compatibility. Take the first step today and give your WordPress website the protection and speed it deserves!


